General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsDianne Feinstein op-ed in the Washington Post
Sen. Dianne Feinstein (D-CA) wrote an op-ed for the Post in which she defended the NSA phone records program and proposes modest reforms about it. You can read it here. In my opinion, it was the usual vague and unconvincing reassurances about how the government and its secret court oversee the program, followed by an allusion to terrorism and how frightening it should be.
However, one section stood out to me:
Only 22 highly vetted NSA analysts can approve a query of this database — and only when they have a reasonable, articulable suspicion that the number is connected to terrorism.
If the NSA analyst believes that circumstances justify the need to know the actual content of the call to probe further into what may be an active terrorist plot, the numbers are sent to the FBI, which requests a warrant from the court that oversees the Foreign Intelligence Surveillance Act (FISA). Ultimately, this court determines if “probable cause” is sufficient to grant the warrant to collect the content of the call.
According to this, the NSA can query its database of phone records. If they determine "the call" is important, they can ask the FISA court for a warrant to listen to "the call". What call is she talking about? It's not previously specified before she refers to it. In particular, is this a call that was made in the past? If so, how could they "collect" the content of it, if they didn't already have it stored somewhere? Do they already have it stored somewhere?
Perhaps this was just poorly phrased, and she means collection of future calls. But I'd really like to know.
Any thoughts?
Savannahmann
(3,891 posts)You see, she just let the cat out of the bag. They do capture and store contents of calls. Which is exactly what they said they did not do. Now, releasing that information, was in fact releasing secret information. So Diane Feinstein just committed Espionage by the definitions tossed about here constantly.
BrotherIvan
(9,126 posts)PowerToThePeople
(9,610 posts)Either she does not understand how it works or she does.
So either she is mistaken and giving false information or
They are recording everything.....
chimpymustgo
(12,774 posts)Major Hogwash
(17,656 posts)And jives with everything we have been told the FISA court does.
grasswire
(50,130 posts)Everything is hoovered up and stored. She's saying that when the need arises, they get a warrant and access the content of the troublesome call that was already stored.
That's her simplistic explanation. Nothing to see here.
reusrename
(1,716 posts)That's the way the law is written and that's also the way Snowden et. al. have described it.
The analyst is used somewhat like a robosigner in this process. He fills out a form or template and the act of completing the form releases the content for review.
Then, sometime within the next 72 hours the warrant is requested from the FISA court. The FISA court automatically approves the warrant request submitted in this manner because the software modules ensure that all legal requirements for the warrant are met during the process of the analyst completing the initial form or template.
So, yes, a warrant is necessary in order to peek at the content.
And, yes, an analyst can look at the stuff on his own authority, without a warrant.
The law gives an analyst legal access to the content, on his own authority, once he has been verbally authorized by either the Director of National Intelligence (Clapper) or the Attorney General (Holder).
pipoman
(16,038 posts)why is it again that we need a "secret court" to issue these warrants? as opposed to our massive federal court system already in place and funded? a court which can ignore the transparency of public records requests? it isn't because federal courts are governed by different laws, to wit: the constitution, Bill of Rights, and the numerous publicly accessible laws, as opposed to secret laws? Do these judges, when sworn in, swear to uphold the Constitution of the United States? What exactly is the oath they take?
struggle4progress
(118,282 posts)had unlimited ability to perform certain wiretapping operations related to national security, and the judicial branch had been upholding him in this regard; to reduce the possibility of further nixonian abuses, the fisa courts were established as a compromise involving all three branches of government in various ways
it's not enough to hold the house, senate, and presidency long enough to re-do the fisa legislation: we need also to hold the senate and presidency long enough to change the long-term complexion of the federal judiciary, so that we won't simply revert to the law according to the nixon-era courts
pipoman
(16,038 posts)inclination whatsoever to "re-do the fisa legislation". Has any meaningful Democrat even suggested such a thing?
alp227
(32,025 posts)I think she's retiring, so California better get a REAL progressive in the senate by 2016!
BrotherIvan
(9,126 posts)The majority of our CA representatives and senators mostly suck.
Luminous Animal
(27,310 posts)Skittles
(153,160 posts)backscatter712
(26,355 posts)Oh, sure, they record and store your phone calls, but they PROMISE they won't listen to them unless one of their elite magic experts concludes you're a terrorist first! ![]()
Life Long Dem
(8,582 posts)Greenwald is that you? ![]()
they record and store your phone calls,
backscatter712
(26,355 posts)dreamnightwind
(4,775 posts)Hard to believe she would just out and say that, but it's pretty clear. And she referenced the "content of the call" twice in that statement, which makes it less likely that it was unintended.
What she described is pretty much how I had thought it might be. They have it all, going back a certain number of years (she say it's a 5-year retention period, though in that statement she says "phone records" so it's unclear if the content has that retention period) only some other agency, contractor, or even telecom company probably collects it so the NSA can kind of say they don't do it. When a person or phone call is flagged (either by profiling/tracking software or by an analyst, it's probably not all automated) they can go get the content from that dataset.
She seems to claim that every request for content first gets approved by FISA, a claim I'm skeptical of.
I could imagine them having some broad outstanding authorizations from the court, so that they don't get every single phone call request reviewed by the court, such a practice could lead to wholesale abuse of the system, though I'm only speculating.
I sure don't think we can just trust them, though, there needs to be real oversight by elected people who are at least supposed to be responsible to the public.
Great find, this seems like a big deal to me. I wouldn't hold my breath for the MSM to make it big news, I guess that's up to us.
K & R
truedelphi
(32,324 posts)Sibel Edmonds' website have stated that the conversations can be re-constituted from the meta data. That the text of the emails can be re-constituted. Going back for years.
And although Di Fi's writing in the OP is a bit ambiguous, Binney and others have spoken very clearly about it.
Edmonds' website is boilingfrogs.com
WillyT
(72,631 posts)dreamnightwind
(4,775 posts)but the metadata is for indexing and profiling, it doesn't contain the content, if it does it isn't metadata it's data, and I'm pretty sure they wouldn't do anything so obvious as to call the actual content metadata. It's the same in the end either way, they have the content stored and a way to get to it.
Oh, and ![]() good to hear from you.
good to hear from you.
davidn3600
(6,342 posts)We are spying on you. We are collecting your data. But we promise not to look into it unless we designate you a terrorist and our secret court says we can.
woo me with science
(32,139 posts)Still the cart before the horse. What a despicable, unconstitutional charade.
They have no right to collect and store the information in the first place.
woo me with science
(32,139 posts)If they weren't, they wouldn't engage in these ridiculous contortions. They wouldn't have to make up absurdities like the "three hop rule" in order to simultaneously claim that they are bound by limits for spying *and* explain why they are surveilling MILLIONS of us.
They are lying brazenly to our faces, again and again and again and again and again, just like their shameless, amoral mouthpieces in the press and across the internet.
They are corrupt, and they are liars.

Catherina
(35,568 posts)vanlassie
(5,670 posts)Major League Warmonger. Supporting women's rights while fucking us ALL.
WCLinolVir
(951 posts)boston bean
(36,221 posts)No one can say they aren't collecting the actual recording of the call, anymore.
This spells it out pretty clearly.
MindPilot
(12,693 posts)This is the boilerplate reply I received from Feinstein in response to my concerns about NSA spying.
> From: <senator@feinstein.senate.gov>
> To: <>
> Subject: U.S. Senator Dianne Feinstein responding to your message
> Date: Wed, 17 Jul 2013 10:19:22 -0400
>
> <http://feinstein.senate.gov/>
>
>
>
> Dear Mindpilot:
>
>
>
> I received your communication indicating your concerns about the two
> National Security Agency programs that have been in the news recently.
> I appreciate that you took the time to write on this important issue
> and welcome the opportunity to respond.
>
>
>
> First, I understand your concerns and want to point out that by law,
> the government cannot listen to an American's telephone calls or read
> their emails without a court warrant issued upon a showing of probable
> cause. As is described in the attachment to this letter provided by
> the Executive Branch, the programs that were recently disclosed have
> to do with information about phone calls - the kind of information
> that you might find on a telephone bill - in one case, and the
> internet communications (such as email) of non-Americans outside the
> United States in the other case. Both programs are subject to checks
> and balances, and oversight by the Executive Branch, the Congress, and
> the Judiciary.
>
>
>
> As Chairman of the Senate Intelligence Committee, I can tell you that
> I believe the oversight we have conducted is strong and effective and
> I am doing my level best to get more information declassified. Please
> know that it is equally frustrating to me, as it is to you, that I
> cannot provide more detail on the value these programs provide and the
> strict limitations placed on how this information is used. I take
> serious my responsibility to make sure intelligence programs are
> effective, but I work equally hard to ensure that intelligence
> activities strictly comply with the Constitution and our laws and
> protect Americans' privacy rights.
>
>
>
> These surveillance programs have proven to be very effective in
> identifying terrorists, their activities, and those associated with
> terrorist plots, and in allowing the Intelligence Community and the
> Federal Bureau of Investigation to prevent numerous terrorist attacks.
> More information on this should be forthcoming.
>
>
>
> • On June 18, 2003, the Director of the National Security Agency (NSA)
> testified to the House Intelligence Committee that there have been
> "over 50 potential terrorist events" that these programs helped
> prevent.
>
>
>
> • While the specific uses of these surveillance programs remain
> largely classified, I have reviewed the classified testimony and
> reports from the Executive Branch that describe in detail how this
> surveillance has stopped attacks.
>
>
>
> • Two examples where these surveillance programs were used to prevent
> terrorist attacks were: (1) the attempted bombing of the New York City
> subway system in September 2009 by Najibullah Zazi and his
> co-conspirators; and (2) the attempted attack on a Danish newspaper
> that published cartoons of the Prophet Mohammed in October 2009 by U.S.
> citizen David Headley and his associates.
>
>
>
> • Regarding the planned bombing of the New York City subway system,
> the NSA has determined that in early September of 2009, while
> monitoring the activities of Al Qaeda terrorists in Pakistan, NSA
> noted contact from an individual in the U.S. that the FBI subsequently
> identified as Colorado-based Najibullah Zazi. The U.S. Intelligence
> Community, including the FBI and NSA, worked in concert to determine
> his relationship with Al Qaeda, as well as identify any foreign or
> domestic terrorist links. The FBI tracked Zazi as he traveled to New
> York to meet with co-conspirators, where they were planning to conduct
> a terrorist attack using hydrogen peroxide bombs placed in backpacks.
> Zazi and his co-conspirators were subsequently arrested. Zazi
> eventually pleaded guilty to conspiring to bomb the NYC subway system.
>
>
>
> • Regarding terrorist David Headley, he was also involved in the
> planning and reconnaissance of the 2008 terrorist attacks in Mumbai,
> India that killed 166 people, including six Americans. According to
> NSA, in October 2009, Headley, a Chicago businessman and dual U.S. and
> Pakistani citizen, was arrested by the FBI as he tried to depart from
> Chicago O'Hare airport on a trip to Europe. Headley was charged with
> material support to terrorism based on his involvement in the planning
> and reconnaissance of the hotel attack in Mumbai 2008. At the time of
> his arrest, Headley and his colleagues were plotting to attack the
> Danish newspaper that published the unflattering cartoons of the
> Prophet Mohammed, at the behest of Al Qaeda.
>
>
>
> Not only has Congress been briefed on these programs, but laws passed
> and enacted since 9/11 specifically authorize them. The surveillance
> programs are authorized by the Foreign Intelligence Surveillance Act
> (FISA), which itself was enacted by Congress in 1978 to establish the
> legal structure to carry out these programs, but also to prevent
> government abuses, such as surveillance of Americans without approval
> from the federal courts. The Act authorizes the government to gather
> communications and other information for foreign intelligence purposes.
> It also establishes privacy protections, oversight mechanisms
> (including court review), and other restrictions to protect privacy
> rights of Americans.
>
>
>
> The laws that have established and reauthorized these programs since
> 9/11 have passed by mostly overwhelming margins. For example, the
> phone call business record program was reauthorized most recently on
> May 26, 2011 by a vote of 72-23 in the Senate and 250-153 in the House.
> The internet communications program was reauthorized most recently on
> December 30, 2012 by a vote of 73-22 in the Senate and 301-118 in the
> House.
>
>
>
> Attached to this letter is a brief summary of the two intelligence
> surveillance programs that were recently disclosed in media articles.
> While I very much regret the disclosure of classified information in a
> way that will damage our ability to identify and stop terrorist
> activity, I believe it is important to ensure that the public record
> now available on these programs is accurate and provided with the
> proper context.
>
>
>
> Again, thank you for contacting me with your concerns and comments. I
> appreciate knowing your views and hope you continue to inform me of
> issues that matter to you. If you have any additional questions or
> concerns, please do not hesitate to contact my office in Washington,
> D.C. at (202) 224-3841.
>
>
>
> Sincerely yours,
>
>
> Dianne Feinstein
> United States Senator
>
leveymg
(36,418 posts)Compare Feinstein's OpEd to the language the President used in describing the way the Sec. 702 system works.
Obama’s Misleading Statement to Charlie Rose: “There is no content in that database”
The President's interview with Rose is excerpted at length, below: http://www.democraticunderground.com/10023050432
Program 215, (the President) said gets data from the service providers like a Verizon in bulk, and basically call pairs.
"Now, if the NSA through some other sources, maybe through the FBI, maybe through a tip that went to the CIA, maybe through the NYPD. Get a number that where there's a reasonable, articulable suspicion that this might involve foreign terrorist activity related to al-Qaeda and some other international terrorist actors.
Then, what the NSA can do is it can query that database to see did this number pop up? Did they make any other calls? And if they did, those calls will be spit out. A report will be produced. It will be turned over to the FBI. At no point is any content revealed because there's no content," Obama explained.
We now see that the President's statement is, at the least, misleading, if not confused: "There is no content in that database."
In fact, both parts – content and metadata - go through a single NSA database, and the NSA slide show that.
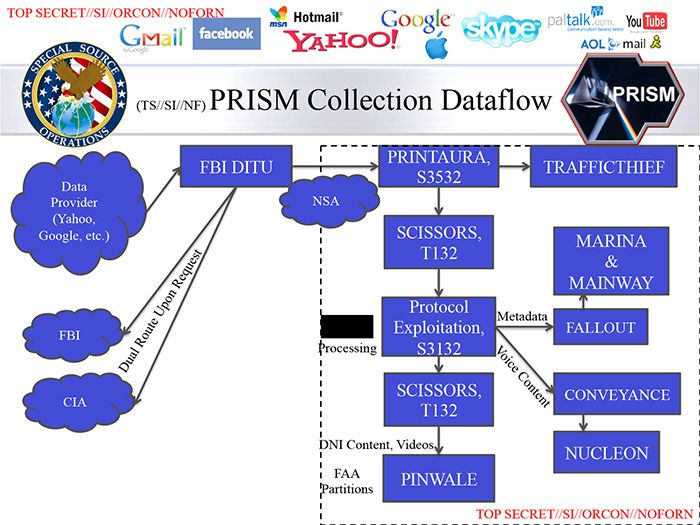
I think what Obama did there was conflate the Sec.702 system (PRISM) with one small part of that database, MARINA (voice) and MAINWAY (email), where metadata is stored. Voice content, meanwhile, goes to NUCLEON, below.
The slide that came out today is referenced below as "DNI Content," and that is the data the analyst can access at the profiling (Target Acquisition) stage in order to determine whether to pass the case over to the FBI for a FISA warrant. That DNI Content in turn goes into the PINWALE database for further analysis.
Igel
(35,309 posts)Start with "the need to know the actual content of the call."
What call? We introduce new topics with "a." There are exceptions--generics, for example, or something that is specific and so "in the context" that it's been introduced. But no call, definite or specific, is in the context. Suspicion: Bad edit.
Or no a very felicitous use of a generic noun. You get to the "the" and you stumble. Some people are clumsy enough not to notice.
Then we get to the phrase "the warrant to collect the content of the call." If it's already collected, why is it being collected? If it's a call that was already made but the content wasn't collected, how do you collect it without a time warp or TARDIS? It's one thing to need a warrant to listen to an already collected call from last week. It's entirely another thing to need a warrant to collect a call from last week.
I think there's a bad edit. There's a category of calls that are collected but not open to the NSA. This has been discussed before. When you have permission to wiretap somebody overseas you sometimes pick up not just foreign nationals calling foreign nationals. And if you know that 999-888-9999 called your terrorist suspect in Peshawar that you're wiretapping it may be handle to search to see if 999-888-9999 placed any other calls to anybody else you've been wiretapping--perhaps a suspect in London. It may be that she's referring to those, because in the NSA slide that is referred to upstream the explanation was precisely this sort of case.
Note that there was a (R) politician from Alaska that was caught in a bribery scandal in this sort of way. A building contractor was wiretapped. In wiretapping the contractor you necessarily also pick up the other person's call. Nobody considered this a breech of the Constitution.
leveymg
(36,418 posts)from the Stevens case.