General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsREPORT: Big Tech Working With Government On Special, Secure Servers Just For Sharing Info
http://www.businessinsider.com/prism-facebook-and-google-secure-servers-just-for-sharing-with-the-government-2013-6
***SNIP
According to Miller, the government does not have direct access, but through negotiations, companies have agreed to set up more efficient systems for sharing data with the government.
Here's the key bit:
...instead of adding a back door to their servers, the companies were essentially asked to erect a locked mailbox and give the government the key, people briefed on the negotiations said. Facebook, for instance, built such a system for requesting and sharing the information, they said.
The data shared in these ways, the people said, is shared after company lawyers have reviewed the FISA request according to company practice. It is not sent automatically or in bulk, and the government does not have full access to company servers.
Instead, they said, it is a more secure and efficient way to hand over the data.
Read more: http://www.businessinsider.com/prism-facebook-and-google-secure-servers-just-for-sharing-with-the-government-2013-6#ixzz2VdNfUQ8O
boston bean
(36,221 posts)leveymg
(36,418 posts)In other words, the companies are giving NSA everything it asks for -- which is everything, if the VERIZON warrant is representative -- but just after the lawyer's have read the Order. But, since the FISA Court orders are ongoing, isn't that the same thing as "direct server access", just through a separate communications channel, the "lock box"?
The conclusion we should draw from this is that NSA is scooping up all data from all sources, and then doing something with it. What might that be? Profiling, of course, otherwise they couldn't handle all that data about so many people. But, everyone gets run through the system to identify persons of interest. Of course. Please, see, http://www.dailykos.com/story/2013/06/07/1214479/-Is-Universal-Profiling-of-phone-users-in-America-the-next-revelation
Luminous Animal
(27,310 posts)Related
Twitter declined to make it easier for the government. But other companies were more compliant, according to people briefed on the negotiations. They opened discussions with national security officials about developing technical methods to more efficiently and securely share the personal data of foreign users in response to lawful government requests. And in some cases, they changed their computer systems to do so.
The negotiations shed a light on how Internet companies, increasingly at the center of people’s personal lives, interact with the spy agencies that look to their vast trove of information — e-mails, videos, online chats, photos and search queries — for intelligence. They illustrate how intricately the government and tech companies work together, and the depth of their behind-the-scenes transactions.
leveymg
(36,418 posts)People shouldn't assume that their data is somehow immune or protected. You'd have to be pretty isolated to not have had any communication with someone abroad in the last five years.
Luminous Animal
(27,310 posts)leveymg
(36,418 posts)But, this as with every other political board like it is just another part of the data stream that goes into the Thin Thread derived program that NSA uses to profile us. ALL OF US. Why do I say that? Because there aren't enough human analysts to read it all, so the system uses an automated scoring system to identify potential targets for closer attention. THAT IS PROFILING.
EVERYONE WHO MAKES A TELEPHONE CALL OR SENDS AN EMAIL OR POSTS ON FACEBOOK (OR ON DU) IS PROFILED. That is by necessity to sort out all the data and make the system work.
FarCenter
(19,429 posts)email address and IP addressess with posting times corresponding to their username, for instance.
leveymg
(36,418 posts)A subpoena is not required for NSA to determine the origination point of on-line posting, which is treated as open source data. All that some analyst needs to do is trace root back to the sender of any particular post. No need to bother a Judge for that sort of thing.
FarCenter
(19,429 posts)leveymg
(36,418 posts)Besides, people who try to set up proxy networks and addresses get first attention from Officer Mike (or an electronic version). Hi, Mike or e-Mike! How's the day goin' fer yal - busy the last few days, I'm sure. Carry on! ![]()
![]()
![]()
DisgustipatedinCA
(12,530 posts)So it's not as though an NSA analyst would see routes change and wonder, hey where did they all go?
On the other hand, almost all business and home customers will have a private address, and many of the will actually have the same address (192.168.1.1 is the most common IPv4 address...comes from default behavior of devices combined with laziness). These "private" addresses are masked behind a real, routeable-on-the-Internet IP address. Oftentimes, many different customers are hidden behind this same address. ZIP codes are roughly analogous...think in terms of lots of different servers sending data to the ZIP Code 47150. All the data is destined for different users in that ZIP Code, but the local postmaster (the ISP) must deliver to the actual customers. This is done with Network Address Translation, which maps the public IP address to the private IP address. The tricky part is that those private addresses can and do change from time to time.
So it does take the cooperation of the ISP, or at least access to their data. It's widely believed that NSA gets this data in firehouse fashion from all major ISP's.
leveymg
(36,418 posts)Last edited Sat Jun 8, 2013, 04:08 PM - Edit history (3)
No need to get the ISP's cooperation. It's usually done without it, except when the ISP or telco needs to get paid (a lot) out of the Justice Dept. fund for a Title III warrant (FBI) connection. Here's how that intercept system works: http://en.wikipedia.org/wiki/Communications_Assistance_for_Law_Enforcement_Act
USA telecommunications providers must install new hardware or software, as well as modify old equipment, so that it doesn't interfere with the ability of a law enforcement agency (LEA) to perform real-time surveillance of any telephone or Internet traffic. Modern voice switches now have this capability built in, yet Internet equipment almost always requires some kind of intelligent Deep Packet Inspection probe to get the job done. In both cases, the intercept-function must single out a subscriber named in a warrant for intercept and then immediately send some (headers-only) or all (full content) of the intercepted data to an LEA. The LEA will then process this data with analysis software that is specialized towards criminal investigations.
All traditional voice switches on the U.S. market today have the CALEA intercept feature built in. The IP-based "soft switches" typically do not contain a built-in CALEA intercept feature; and other IP-transport elements (routers, switches, access multiplexers) almost always delegate the CALEA function to elements dedicated to inspecting and intercepting traffic. In such cases, hardware taps or switch/router mirror-ports are employed to deliver copies of all of a network's data to dedicated IP probes.
Probes can either send directly to the LEA according to the industry standard delivery formats (c.f. ATIS T1.IAS, T1.678v2, et al.); or they can deliver to an intermediate element called a mediation device, where the mediation device does the formatting and communication of the data to the LEA. A probe that can send the correctly formatted data to the LEA is called a "self-contained" probe.
In order to be compliant, IP-based service providers (Broadband, Cable, VoIP) must choose either a self-contained probe (such as made by IPFabrics), or a "dumb" probe component plus a mediation device (such as made by Verint, or they must implement the delivery of correctly formatted for a named subscriber's data on their own.
Here's some additional information on the role that CALEA-compliant equipment plays in PRISM and some other NSA programs: http://www.guardian.co.uk/world/2013/jun/07/nsa-prism-records-surveillance-questions
The NSA isn't saying. Sources in the data-processing business point to a couple of methods. First, lots of data bound for those companies passes over what are called "content delivery networks" (CDNs), which are in effect the backbone of the internet. Companies such as Cisco provide "routers" which direct that traffic. And those can be tapped directly, explains Paolo Vecchi of Omnis Systems, based in Falmer, near Brighton.
"The Communications Assistance for Law Enforcement Act (Calea) passed in 1994 forces all US manufacturers to produce equipment compliant with that law," says Vecchi. "And guess what: Cisco is one of the companies that developed and maintains that architecture." Cisco's own documents explain its Calea compliance.
So the NSA would only need to tap the routers?
Not quite. Much of the traffic going to the target companies would be encrypted, so even when captured it would look like a stream of digital gibberish. Decrypting it would require the "master keys" held by the companies.
Did the companies know?
They say not. Those which have been contacted have all denied knowledge of it: Google, for example, said: "Google does not have a 'back door' for the government to access private user data." An Apple spokesman said: "We have never heard of Prism. We do not provide any government agency with direct access to our servers and any agency requesting customer data must get a court order."
The Washington Post retracted part of its story about Prism in which it said that the companies "knowingly" participated. Instead, it quotes a report which says that "collection managers [could send] content tasking instructions directly to equipment installed at company-controlled locations".
It is ambiguous whether "company" refers to the NSA or the internet companies. But the implication seems to be that the NSA has been running a system that can tap into the internet when it wants.
How could the companies not know if they had provided master decryption keys?
They might be required to provide them under US law, but would not be allowed to disclose the fact. That would give the NSA all it needed to monitor communications.
DisgustipatedinCA
(12,530 posts)I don't doubt they can crack SSL, but they can't do it in a timely manner, so I'm guessing cooperation is still required foe encrypted sessions.
leveymg
(36,418 posts)Last edited Sat Jun 8, 2013, 03:11 PM - Edit history (1)
most compelling NSA arguments for universal interception and storage is the practice by sophisticated adversaries of enslaving many computers with trojans and using each to transmit only tiny partial bursts of encrypted messages.
If you can't read the entire network of slave computers, you won't crack the message, or so the argument goes.
Personally, I find this a compelling technical argument for NSA interception and storage, but I don't think it's necessary to profile everyone to manage this sort of decryption task. The claims that are being made for PRISM efficacy are very weak compared to the costs in public revenue and lost privacy of universal profiling. Please, see, http://www.buzzfeed.com/bensmith/public-documents-contradict-claim-email-spying-foiled-terror
FarCenter
(19,429 posts)This may be from a block owned by your organization, assigned by the ISP, or NATted by a firewall or router depending on your situation. If it is assigned by the ISP using DHCP, it will likely change when your lease is up.
So if the investigator has the IP address you were coming from when you posted, he may do an lookup in whois and then follow up with the organization that owns the IP block to find out who it was assigned to at the time of posting. They will then consult their records or logs as appropriate.
DisgustipatedinCA
(12,530 posts)Ohio Joe
(21,751 posts)EDI - Electronic Data Interchange.
The way this works in general... One partner sends a request through the EDI mailbox, the second partner pulls that request into their system and (by various methods) the request is reviewed by the second partner. Once the request is approved, the request is extracted by the second partner and sent to the mailbox where the first partner can pull the data.
I've used this type of method through many systems, it is secure and efficient, and does not grant unfettered access. It is a method of transmitting data, not a determination of what data is sent and in no way indicates anything (one way or the other) about what/how much data is given.
leveymg
(36,418 posts)The data coming from the company to NSA needs to be copied, tagged, and distributed, so I'm not sure that it's really EDI which usually is bound by an electronic form or template that isn't meant to be directly viewed by personnel.
Ohio Joe
(21,751 posts)It has formats for pretty much everything, it's been around a long time (I first used it in 93... maybe 94). My point is... They are describing a delivery method and that tells you zero about the contents except that it is very secure. If what is being delivered is everything or if it is the bare minimum required it would require the same level of security so... This story says nothing to me and is evidence of nothing one way or the other.
leveymg
(36,418 posts)or whatever other programs this is going into.
Ohio Joe
(21,751 posts)The companies admit they send whatever data they are bound to by law. That data is being sent is not in dispute... The real question is how much data? Unfortunately, the delivery method does not do anything to inform that question.
leveymg
(36,418 posts)ations and transactions, particularly if NSA (and client agencies) are data-mining and profiling, as they appear to be. The bigger the data set, the more accurate the algorithm each person gets, and the more reliable the predictive index that triggers a warrant request.
Or, so it would seem. They've had more than a decade to develop this thing since it went operational.
Ohio Joe
(21,751 posts)Or... It might not be. Again, my point is that delivery method does not inform content.
If I tell you I sent my friend a package via UPS with some books... Can you tell how many books or what the books are about?
We have known for a long time that 'some data' has been being sent... Getting the information on how it is being sent tells us little more (in this case, that it is being sent in a secure manner) and still nothing regarding the content.
leveymg
(36,418 posts)and mortar address, the originators ISP address, the computer's registration data, etc. NSA also gets most of that through the back doors in the customer's computer OS, as well.
Ohio Joe
(21,751 posts)You are still trying to determine content from the delivery method... It can't be done. Everything you list is speculation about content and the fact is, we do not yet know the content.
"NSA also gets most of that through the back doors in the customer's computer OS, as well."
Sigh... OK, off we go to fantasy land. Logic... If they had a back door with unfettered access, they would never have asked for anything or set up a delivery method. I'm not going to start debating conspiracy non-sense, I prefer facts and the bottom line fact here is that this story does not tell us anything except to confirm data is being sent.
leveymg
(36,418 posts)What did Microsoft Corp. have in '07 that NSA wanted most? What does Apple have that they finally let NSA have last year?
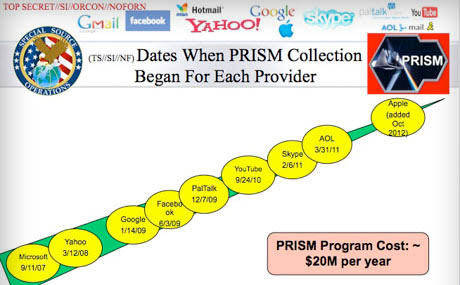
Ohio Joe
(21,751 posts)There is proof that MS gave un-fettered access... Or that all machines have a secret backdoor for the government... Or that delivery method informs content... They really need to start teaching critical thinking in school.
There was one patch released during the NT product cycle where a debug version of the crypto library was reported to contain a variable named NSA_KEY.
leveymg
(36,418 posts)That crudely laid-out picture charts out the corporations that NSA has access to their databases, and when the companies granted permission. What does that tell you?
Ohio Joe
(21,751 posts)"That crudely laid-out picture charts out the corporations that NSA has access to their databases, and when the companies granted permission. What does that tell you?"
It does not say the NSA had access, it says "When collection began". You still have zero that informs content or access ability.
Q: What does that tell you?
A: That data is being sent and nothing more.
Here is one more question... Why do people insist on deciding they know more then facts present instead of try to get more facts?
nebenaube
(3,496 posts)If there was no obvious delivery method then the backdoor would be difficult to deny.
Ohio Joe
(21,751 posts)If a house has a backdoor where people could steal from, does that tell you the contents of an envelope they mailed? The answer is no, it does not.
If however, I enter house via said backdoor, and examine the pad of paper that was used to create the letter that was in the envelope, do I not know something about the content of that envelope?
Ohio Joe
(21,751 posts)Remember, the thief and the person receiving the letter are one and the same. All this OP is talking about is delivery method... Not content. The result is that people are deciding that content can be determined by delivery method... It can't. All manner of conspiracy non-sense when the reality is... The letter is coming to them, they have no need to break in to find out the contents.
'WE', on the other hand, should know what the contents are... Some say it is selected meta-data that there are warrants for... Some say it is everything... Some say other things. The fact is, they are ALL liars so we have no idea what the contents are, simply that something is being sent. No more can be determined at this time.
nebenaube
(3,496 posts)What they are saying is that a collection of meta-data (facts) may relate to each other via enough is-a and has-a relationships and when what the overall context of the is-a or has-a relationship(s) becomes obvious, the need for specific content associated with that meta-data is irrelevant to forming the inference; at least for where the purpose of filtering large amounts of data down to manageable amount of data is concerned.
Ohio Joe
(21,751 posts)I am discussing how the METHOD (hint, what the OP posted, what my fuck original comment was about) used to send the data says nothing about the data and you keep going off on what meta-data can tell you. Let me know when you can wrap your head around the word METHOD and I'll continue, otherwise I'm done with stupid.
suffragette
(12,232 posts)And which lockbox would truly provide more security for the people?
leveymg
(36,418 posts)Can't have guns and butter. We have to "make difficult choices", as the President reminded us all yesterday.
suffragette
(12,232 posts)Into an ever larger surveillance and security apparatus.
It keeps increasing even as the cyclical calls for austerity cuts go on.
wandy
(3,539 posts)For every lock theirs about a hundred criminal lock picks.
Think Malware, Trojans, Chinese all that good stuff.
I lied about making you feel better. ![]()