General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsNetwork security techies: see if this will send a chill up your spine
http://arstechnica.com/security/2015/03/mysterious-snafu-hijacks-uk-nukes-makers-traffic-through-ukraine/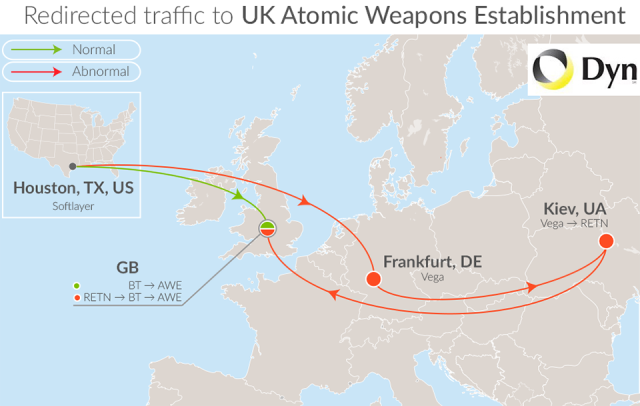
Internet traffic for 167 important British Telecom customers—including a UK defense contractor that helps deliver the country's nuclear warhead program—were mysteriously diverted to servers in Ukraine before being passed along to their final destination.
The snafu may have allowed adversaries to eavesdrop on or tamper with communications sent and received by the UK's Atomic Weapons Establishment, one of the affected British Telecom customers. Other organizations with hijacked traffic include defense contractor Lockheed Martin, Toronto Dominion Bank, Anglo-Italian helicopter company AgustaWestland, and the UK Department for Environment, according to a blog post published Friday by researchers from Dyn, a firm that helps companies monitor and control their online infrastructure.
The diverted traffic appeared to be used to send e-mail and route virtual private networks, as well as for other purposes. As the picture above illustrates, the roundabout path caused the data to travel thousands of miles to the Ukrainian capital of Kiev before turning around, retracing that route, and being delivered to its normal hub in London. Unnecessarily sending the data to Kiev may have made it possible for employees with privileged network access to Ukrainian telecom provider Vega to monitor or tamper with data that wasn't encrypted end-to-end using strong cryptography. The hijacking of the Atomic Weapons Establishment, Lockheed, and the other 165 routes occurred over a 90-minute span on Thursday, while a handful of British Telecom customers experienced diverted traffic for five days beginning Saturday.
"The 167 hijacked prefixes (listed below) also included more innocuous networks like those of Pepsi Cola (165.197.56.0/22) and Wal-Mart UK (161.163.166.0/24 and 161.163.177.0/24)," Dyn Director of Internet analysis Doug Madory wrote. "However, these networks do host domains with 'VPN' and 'mail' in their names, implying they provide important services for these companies. Does this list represent some curious mistake or something more? Either way, it redirected a portion of Internet traffic bound for networks, at a minimum resulting in poor performance for some customers."
Snip
valerief
(53,235 posts)LiberalArkie
(15,715 posts)Everything used to be run on T-1's to ds-3 dedicated circuits. Pretty damn secure point to point stuff. It really scared me when everything started going to AT&T cloud, Level-3 Cloud etc. The switch geeks would always say "Its secure its VPN", I thought BS. With a lot of the Snowden docs showing that the VPN's are compromised, I wonder when there will be a trillion dollar theft, may have happened already, how would we taxpayers know.
JustAnotherGen
(31,813 posts)Former GC Carrier A.M. Here. I went into M &P s in marketing to build the processes surrounding colos and terrestrial and subsea pl's because I had managed more pl installations in one year than folks who had been there for years. When executed accurately - they were truly private lines.
riderinthestorm
(23,272 posts)Poor performance??!! That's what they're worried about.
I'm not even a techie and I can see this as being very worrisome.
dorkzilla
(5,141 posts)At least in this country, you cannot monitor domestic traffic legally so it's diverted and monitored elsewhere. It's just a way to get around the law. Nice, huh?
Cryptoad
(8,254 posts)redirecting walmart email to Comrade snowden,,,,,,, yall crack me up.