Newly Released NSA Slides Explain the PRISM Data-Collection Program
Source: Washington Post
@BreakingNews: Newly released NSA slides detail how program interacts with internet companies - @washingtonpost http://t.co/qSk7U1F7RV
NSA slides explain the PRISM data-collection program
Published: June 6, 2013, Updated: June 29, 2013
The top-secret PRISM program allows the U.S. intelligence community to gain access from nine Internet companies to a wide range of digital information, including e-mails and stored data, on foreign targets operating outside the United States. The program is court-approved but does not require individual warrants. Instead, it operates under a broader authorization from federal judges who oversee the use of the Foreign Intelligence Surveillance Act (FISA). Some documents describing the program were first released by The Washington Post on June 6. The newly released documents below give additional details about how the program operates, including the levels of review and supervisory control at the NSA and FBI. The documents also show how the program interacts with the Internet companies. These slides, annotated by The Post, represent a selection from the overall document, and certain portions are redacted. Read related article.
New slides published June 29
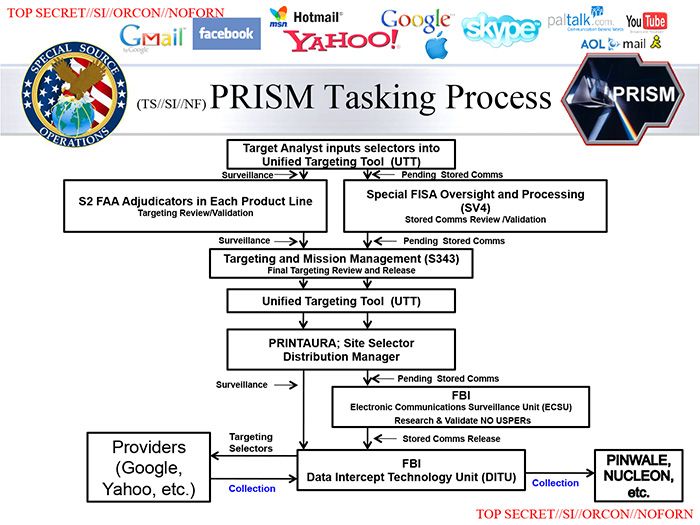
Acquiring data from a new target
This slide describes what happens when an NSA analyst "tasks" the PRISM system for information about a new surveillance target. The request to add a new target is passed automatically to a supervisor who reviews the "selectors," or search terms. The supervisor must endorse the analyst's "reasonable belief," defined as 51 percent confidence, that the specified target is a foreign national who is overseas at the time of collection.
[/B[Analyzing information collected from private companies
After communications information is acquired, the data are processed and analyzed by specialized systems that handle voice, text, video and "digital network information" that includes the locations and unique device signatures of targets.
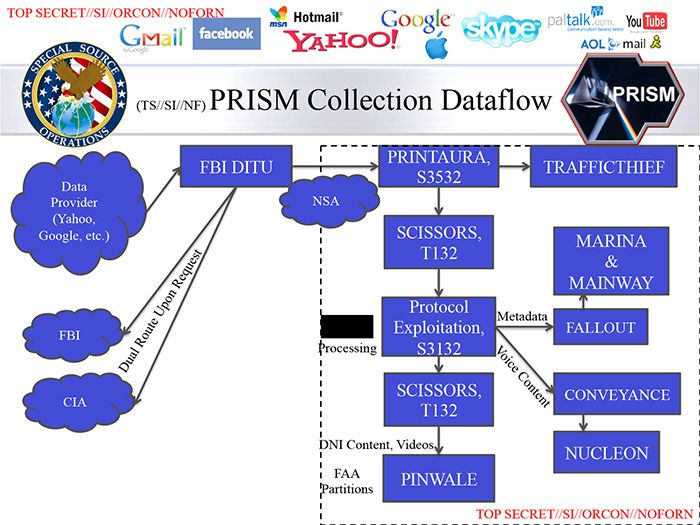
Each target is assigned a case notation
The PRISM case notation format reflects the availability, confirmed by The Post's reporting, of real-time surveillance as well as stored content.

Read more: http://www.washingtonpost.com/wp-srv/special/politics/prism-collection-documents/m/
NoOneMan
(4,795 posts)Participating in this false electronic utopia only strengthens the state's control of you. You are being reduced to a statistic. A cog in a machine that provides production. Yet you are watched, so that if you ever turn on the machine it will be able to cost-effectively eliminate you as an undesirable. Are the benefits of texting, chatting, liking, plusing, etc, really justifying your participation in this ubiquitous system that only enjoys you insofar as your existence is cost-effective to the overall apparatus?
There are other ways to think and be. There is life beyond the Twitterverse. There is more to human existence. Its never been a better time to turn off your computer, drop acid, fuck and tune in the the natural harmony of the world. And with the empire in decline and the environment spelling doom, why not live a little (and no, I mean really live--not read a Facebook post). Fuck this bullshit.
leveymg
(36,418 posts)this ubiquitous system that only enjoys you insofar as your existence is cost-effective to the overall apparatus
The difference between that fantasy and the real world is that they don't stop chasing you when the cost exceeds your value. That's the lesson of the system we live in, it surveils, polices, tortures, and imprisons for its own sake, and even makes a profit. It commoditizes terrorism and crime. Unlike the movie, dropping out and running makes no difference.

Enthusiast
(50,983 posts)leveymg
(36,418 posts)In addition to NUCLEON, there is a second voice data program named CONVEYANCE. Obviously, voice content is being acquired as part of the same program. They appear to still be lying to us.
Metadata goes to MARINA and MAINWAY.
wtmusic
(39,166 posts)Drip...drip...drip....
leveymg
(36,418 posts)There is no other category that voice data might fit into. Note also that Stored Data is shown to be in the PRISM database (SLIDES 1 and 2)
leveymg
(36,418 posts)STORED COMMS - this seems to confirm that the voice and email content are already in the system, and not acquired by a separate survillance process. The system apparently just pulls the content along with the metadata out of the same database.
Obama said "there's nothing" in there except metadata.
pnwmom
(108,973 posts)Obama was talking about internal US surveillance.
leveymg
(36,418 posts)these slide show that, as explained below. Do you want to know what Obama actually said?
Much of the President's credibility on this issue rides on the accuracy of his assertions made to Charley Rose that NSA's "2015 program" keeps only phone call metadata and does not collect voice content. As he put it, the NSA doesn't listen to Americans phone calls because that data isn't kept. "There is no content. " But, is that true? The Post's revelation about NUCLEON certainly contributes to the doubts about that claim.
The President's interview with Rose is excerpted at length, below: http://www.democraticunderground.com/10023050432Program 2015, (the President) said gets data from the service providers like a Verizon in bulk, and basically call pairs.
"You have my telephone number connecting with your telephone number. There are no names. There is no content in that database. All it is, is the number pairs, when those calls took place, how long they took place. So that database is sitting there," he said.
"Now, if the NSA through some other sources, maybe through the FBI, maybe through a tip that went to the CIA, maybe through the NYPD. Get a number that where there's a reasonable, articulable suspicion that this might involve foreign terrorist activity related to al-Qaeda and some other international terrorist actors.
Then, what the NSA can do is it can query that database to see did this number pop up? Did they make any other calls? And if they did, those calls will be spit out. A report will be produced. It will be turned over to the FBI. At no point is any content revealed because there's no content," Obama explained.
We now see that the President's statement is, at the least, misleading, if not confused: "There is no content in that database."
pnwmom
(108,973 posts)However, you didn't prove that there IS content in the database.
Hint: "contributing to doubts" doesn't equal proof.
leveymg
(36,418 posts)"Content Type: STOREDCOMS" category, which can only be voice content from all those calls scooped up with driftnet warrants at telco switches.
leveymg
(36,418 posts)This appears to answer some of the issue of whether analysts can access communications in real-time, or whether they have to wait for a warrant. That question was raised by this report in CNET: http://news.cnet.com/8301-13578_3-57589495-38/nsa-spying-flap-extends-to-contents-of-u.s-phone-calls/
Rep. Jerrold Nadler, a New York Democrat, disclosed on Thursday that during a secret briefing to members of Congress, he was told that the contents of a phone call could be accessed "simply based on an analyst deciding that."
If the NSA wants "to listen to the phone," an analyst's decision is sufficient, without any other legal authorization required, Nadler said he learned. "I was rather startled," said Nadler, an attorney and congressman who serves on the House Judiciary committee.
Not only does this disclosure shed more light on how the NSA's formidable eavesdropping apparatus works domestically, it also suggests the Justice Department has secretly interpreted federal surveillance law to permit thousands of low-ranking analysts to eavesdrop on phone calls.
James Owens, a spokesman for Nadler, provided a statement on Sunday morning, a day after this article was published, saying: "I am pleased that the administration has reiterated that, as I have always believed, the NSA cannot listen to the content of Americans' phone calls without a specific warrant." Owens said he couldn't comment on what assurances from the Obama administration Nadler was referring to, and said Nadler was unavailable for an interview. (CNET had contacted Nadler for comment on Friday.)
Because the same legal standards that apply to phone calls also apply to e-mail messages, text messages, and instant messages, being able to listen to phone calls would mean the NSA analysts could also access the contents of Internet communications without going before a court and seeking approval.
Bear in mind two things: the system seems to handle phone and email messages differently, and under FISA as revised by the PATRIOT ACT, NSA analysts and contractors have 72 hours to do what they want with all data before seeking a warrant. A warrant is only required if the decision is made to target the individual.
pnwmom
(108,973 posts)telephone metadata, but requires a warrant to wiretap.
A separate program, the PRISM program described in the OP, involves foreign targets, and collects various forms of content in addition to metadata.
leveymg
(36,418 posts)pnwmom
(108,973 posts)dkf
(37,305 posts)How in the world does an internal agency get the authorization for mass blanket collection?
wtmusic
(39,166 posts)I wish people would get over this administration-generated nonsensical meme that metadata is "ok" to collect.
Interception of any data whatsoever not related to foreign intelligence is a crime. Period.
leveymg
(36,418 posts)all callers, and these panels do not indicate that there's any clear separation, or splitting off, of email content from metadata, as there seems to be for the path taken by phone communications from the database to the analyst.
The problem with profiling is this: even though the content of phone messages is supposed to be segregated within the databank, the system relies upon algorithms that are built upon all sources of information -- including other US and foreign intel agencies -- to identify possible terrorists. Those other databases (CIA, FBI, MI6, Saudi MID) don't reliably separate (or minimize) US person from foreign person information, so the profiling step has no 4th Amendment protections built into it at all.
In other words, when you place a call, you're being profiled with an NSA "database of databases" that makes no distinctions between US and foreign persons until at a later stage, the software or an analyst determines the caller isn't a likely terrorist or a foreign person.
wtmusic
(39,166 posts)Reading or interpreting the data is not required. If it doesn't involve foreign governments or those acting on their behalf, it's a crime.
There is a small amount of leeway granted for "inadvertent" collection, but there absolutely no way that excuse would hold up in court with the kind of dragnet described here.
leveymg
(36,418 posts)benh57
(141 posts)MANY news organizations are confusing the two. There were 2 totally separate programs leaked
- Verizon phone call metadata going to the govt
- PRISM (full data collection from internet companies) -- these internet companies pass calls, too, like skype and google voice.
leveymg
(36,418 posts)is part of PRISM and is either "processed" when "released" to the analyst or ends up in MARINA, where it is stored. Also see Slide 3, content type "A. STORED COMMS."
I agree, however, that US person telco content is supposed to be minimized under Sec. 215 of the PATRIOT Act. Sec. 216 is supposed to do the same for US person Internet records. Meanwhile Sec. 702 of the 2008 FAA (FISA Amendent Act) legalized the sort of targeted NSA activities that PRISM carries out, but that is supposed to be restricted to foreign persons abroad. But, because of the loopholes in the law -- such as the allowance under 50 USC for 7 days of unfettered viewing of US person data that has been worked into PRISM's profiling step -- it does not look like the wall that is supposed to separate the two programs has any real separation.
secondvariety
(1,245 posts)Last edited Sat Jun 29, 2013, 09:19 PM - Edit history (1)
Too bad the NSA slides seem to be written in a made up language.
JDPriestly
(57,936 posts)Do terrorists communicate via Google or Facebook, etc.?
I heard that they have their own communications services that are encrypted. Is that just a rumor?
I note that the 20 million dollars divided by the number of people under surveillance comes out to about $170 per person? Again, is my math wrong?
I also note that numbers of companies from which data is collected has dramatically increased under the Obama administration
I also note that about 2,353 people per state (50 states and 117,675, are being watched under this program subjects in the database.
The article points out that lots of other people are spied upon because the 2,353 is just the target number. It doesn't include the contacts of the targets.
Apple was just added in 2012.
I take it that the information in the Washington Post only counts American surveillance because Europe has different internet companies. For example:
http://en.wikipedia.org/wiki/List_of_cable_Internet_providers#Belgium
wtmusic
(39,166 posts)NBachers
(17,096 posts)But it just looks like a patch on the arm of some tired bleary-eyed securocrat at a dim dusty console.
![]()
wtmusic
(39,166 posts)but I think I would have ratted out just for having to look at that amateurish interface day after day.
kitt6
(516 posts)Lets say I am gay white. And my lover who lives in Texas, (with Slick Rick) is Black with or without I.D. Can we get married; can he/she vote? America has gone to the Dogs. And I don't mean the Santorum, Rand Paul Dogs.
Ash_F
(5,861 posts)How is that even possible?
leveymg
(36,418 posts)On June 19, I pointed out that the existence of the NUCLEON voice program, which was revealed earlier, appeared to contradict Obama's statement to Charlie Rose a couple nights earlier: http://www.democraticunderground.com/10023050432
QUITE THE OPPOSITE - As this set of slide now demonstrates, PRISM contains voice content and email, as well as metadata. Summary of notes, below. I welcome comments and any reasonable contrary interpretation.
"PRINTAURA automates the traffic flow. SCISSORS and Protocol Exploitation sort data types for analysis in NUCLEON (voice), PINWALE (video), MAINWAY (call records) and MARINA (Internet records)."
In addition to NUCLEON, there is a second voice data program named CONVEYANCE. Obviously, voice content is being acquired as part of the same program. They appear to still be lying to us.
Metadata goes to MARINA and MAINWAY.
NOTE SLIDE 3: Voice data appears to be Content Type: STORED COMMS (Except VoIP)
There is no other category that voice data might fit into. Note also that Stored Data is shown to be in the PRISM database (SLIDES 1 and 2)
NOTE SLIDE 7: EMAIL and CHAT are included in PRISM database. Distinction between SURVEILLANCE and
STORED COMMS - this seems to confirm that the voice and email content are already in the system, and not acquired by a separate survillance process. The system apparently just pulls the content along with the metadata out of the same database.
Obama said "there's nothing" in there except metadata. Apparently not.
pnwmom
(108,973 posts)The top-secret PRISM program allows the U.S. intelligence community to gain access from nine Internet companies to a wide range of digital information, including e-mails and stored data, on foreign targets operating outside the United States.
By contrast, the internal US surveillance Obama was talking about doesn't collect content without a warrant; only telephone metadata.
leveymg
(36,418 posts)pnwmom
(108,973 posts)leveymg
(36,418 posts)how "it doesn't show that." We await a sensible, fact-based reply.
pnwmom
(108,973 posts)Kolesar
(31,182 posts)While the other puppies bark at every leaf that blows across the driveway.
PSPS
(13,583 posts)You can't reason with a member of a personality cult.
leveymg
(36,418 posts)on the side of those who point out how the President and top officials have lied, and the personality cult is clearly those who continue to raise non sequitors in their defense, no matter that the evidence is now clear they have misled the American people about the nature and operation of this program.
Loyalty is nice, but truth is more important.
Godhumor
(6,437 posts)Even your other comment doesn't make it so. One of the slides published says right on it that the counterterrorism database had info on 117,000. Nowhere does it say that says is already pulled, profiled, etc. In fact, it looks like the request for info on an individual from the companies doesn't even occur until after an analyst gives a 51% assessment. Show me anywhere in the slides, specifically, that show everyone is being profiled every time they make a phone call, as you assert in your other post. From the slides presented in the OP, can you prove it?
leveymg
(36,418 posts)Last edited Sun Jun 30, 2013, 08:46 AM - Edit history (1)
If each of those 117K targeted talked to 30 people that month, who in turn talked to 30, that's works out to a bit over 90 million investigations the system runs each month
But, it's worse than that, because the system as its described looks at metadata for each and every call made to see if it connects with any of those 117K and the 875,000 names who are somehow listed in US government databases as suspected of terrorist ties. http://www.reuters.com/article/2013/05/03/us-usa-security-database-idUSBRE94200720130503
By Mark Hosenball
WASHINGTON | Thu May 2, 2013 8:06pm EDT
(Reuters) - The number of names on a highly classified U.S. central database used to track suspected terrorists has jumped to 875,000 from 540,000 only five years ago, a U.S. official familiar with the matter said.
Among those was suspected Boston Marathon bomber Tamerlan Tsarnaev, whose name was added in 2011. The increase in names is due in part to security agencies using the system more in the wake of the failed 2009 attack on a plane by "underpants bomber" Umar Farouk Abdulmutallab in Detroit.
One has to ask, if the government already knows the identities of the real terrorists, what's the point of operating this profiling system?
pnwmom
(108,973 posts)"The top-secret PRISM program allows the U.S. intelligence community to gain access from nine Internet companies to a wide range of digital information, including e-mails and stored data, on foreign targets operating outside the United States."
This isn't what they told us at first. How did the WA Post get it so wrong? Did Snowden wrongly tell them that it involved US internal surveillance or did they draw that incorrect conclusion themselves?
leveymg
(36,418 posts)Get it through your head - the two systems are part of the same database.
The PRISM system is actually a huge database and profiling system for all callers. If your call metadata raises a red flag, the system alerts the human operators, who have 72 hours to download all the data -- including phone and email content -- and then decide whether to target the callers with a warrant. The profiling has already been carried out by the time the targeting decision is made. The determination that one party to that call is a foreign person is just one factor in that decision.
There are other agencies that operate profiling systems and databases, as yet unrevealed, that can also also target you. They are all interconnected This is just NSAs biggest program.
You're being profiled every time you make a call.
pnwmom
(108,973 posts)that claims the NSA is going directly into the main servers of the 9 companies, and that's been debunked.
leveymg
(36,418 posts)fact that NSA is operating a universal surveillance and profiling system, and this is it.
wtmusic
(39,166 posts)This is the cream of the crop of American programmers?
"If the total count is much less than this, REPRISMFISA is having problems. Email the REPRISMFISA Help Desk at XXX@XXXX.XXX AND INFORM THEM"
![]()
They should be jailed for incompetence, if nothing else.
wtmusic
(39,166 posts)(from the comments)
GeorgeGist
(25,315 posts)this is The Onion!
think
(11,641 posts)As it all still seems a bit surreal...
DirkGently
(12,151 posts)Well, that's a little higher than my confidence the other 49%+??? of information is being handled responsibly.
Grassy Knoll
(10,118 posts)How Ironic.
kitt6
(516 posts)It will be Armchair Aerobics. American style. I'm thinking with a bit of meditation in it. ![]()
Coccydynia
(198 posts)PSPS
(13,583 posts)Of course, it's really OK for all of this to be happening because (pick one):
1. This is nothing new
2. I have nothing to hide
3. What are you, a freeper?
4. But Obama is better than Christie/Romney/Bush/Hitler
5. Greenwald/Flaherty/Gillum/Apuzzo/Braun is a hack
6. We have red light cameras, so this is no big deal
7. Corporations have my data anyway
8. At least Obama is trying
9. This is just the media trying to take Obama down
10. It's a misunderstanding/you are confused
11. You're a racist
12. Nobody cares about this anyway / "unfounded fears"
13. I don't like Snowden, therefore we must disregard all of this
idwiyo
(5,113 posts)PS
NoodleyAppendage
(4,619 posts)By JAMES RISEN and ERIC LICHTBLAU
Published: June 16, 2009
WASHINGTON — The National Security Agency is facing renewed scrutiny over the extent of its domestic surveillance program, with critics in Congress saying its recent intercepts of the private telephone calls and e-mail messages of Americans are broader than previously acknowledged, current and former officials said.
The agency’s monitoring of domestic e-mail messages, in particular, has posed longstanding legal and logistical difficulties, the officials said.
Since April, when it was disclosed that the intercepts of some private communications of Americans went beyond legal limits in late 2008 and early 2009, several Congressional committees have been investigating. Those inquiries have led to concerns in Congress about the agency’s ability to collect and read domestic e-mail messages of Americans on a widespread basis, officials said. Supporting that conclusion is the account of a former N.S.A. analyst who, in a series of interviews, described being trained in 2005 for a program in which the agency routinely examined large volumes of Americans’ e-mail messages without court warrants. Two intelligence officials confirmed that the program was still in operation.
Both the former analyst’s account and the rising concern among some members of Congress about the N.S.A.’s recent operation are raising fresh questions about the spy agency.
http://www.nytimes.com/2009/06/17/us/17nsa.html?_r=0
fasttense
(17,301 posts)You are a product line, I'm a product line, we are all just products up for sale. Welcome to the inevitable results of capitalism.
DCBob
(24,689 posts)you may not like and looks really scary but... its legal.
leveymg
(36,418 posts)in a creepy, technocratic way.
Now that we can look back 5 years, and see that the system has done not much at all to "Keep America Safe," -- and actually operates to profile EVERYONE without probable cause -- it's time to make some changes.