Welcome to DU!
The truly grassroots left-of-center political community where regular people, not algorithms, drive the discussions and set the standards.
Join the community:
Create a free account
Support DU (and get rid of ads!):
Become a Star Member
Latest Breaking News
General Discussion
The DU Lounge
All Forums
Issue Forums
Culture Forums
Alliance Forums
Region Forums
Support Forums
Help & Search
General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsMalwarebytes Advisory: New Sodinokibi ransomware attempts to fill GandCrab void
.
Sodinokibi ransomware, also known as Sodin and REvil, is hardly three months old, yet it has quickly become a topic of discussion among cybersecurity professionals because of its apparent connection with the infamous-but-now-defunct GandCrab ransomware.
Detected by Malwarebytes as Ransom.Sodinokibi, Sodinokibi is a ransomware-as-a-service (RaaS), just as GandCrab was, though researchers believe it to be more advanced than its predecessor. We’ve watched this threat target businesses and consumers equally since the beginning of May, with a spike for businesses at the start of June and elevations in consumer detections in both mid June and mid July. Based on our telemetry, Sodinokibi has been on rise since GandCrab’s exit at the end of May.
.
.
Putting a spin on an old product is a concept not unheard of in legitimate business circles. Often, spinning involves creating a new name for the product, some tweaking of its existing features, and finding new influencers—”affiliates” in the case of RaaS operations—to use (and market) the product. In addition, threat actors would initially limit the new product’s availability and follow with a brand-new marketing campaign—all without touching the product standard. In hindsight, it seems the GandCrab team has taken this route.
A month before the GandCrab retirement announcement, Cisco Talos researchers released information about their discovery of Sodinokibi. Attackers manually infected the target server after exploiting a zero-day vulnerability in its Oracle WebLogic application.
To date, six versions of Sodinokibi has been seen in the wild.
https://blog.malwarebytes.com/threat-spotlight/2019/07/threat-spotlight-sodinokibi-ransomware-attempts-to-fill-gandcrab-void/
Read more about the symptoms and remediation at the link.
.
InfoView thread info, including edit history
TrashPut this thread in your Trash Can (My DU » Trash Can)
BookmarkAdd this thread to your Bookmarks (My DU » Bookmarks)
3 replies, 758 views
ShareGet links to this post and/or share on social media
AlertAlert this post for a rule violation
PowersThere are no powers you can use on this post
EditCannot edit other people's posts
ReplyReply to this post
EditCannot edit other people's posts
Rec (10)
ReplyReply to this post
3 replies
 = new reply since forum marked as read
Highlight:
NoneDon't highlight anything
5 newestHighlight 5 most recent replies
= new reply since forum marked as read
Highlight:
NoneDon't highlight anything
5 newestHighlight 5 most recent replies
Malwarebytes Advisory: New Sodinokibi ransomware attempts to fill GandCrab void (Original Post)
TheBlackAdder
Jul 2019
OP
RKP5637
(67,109 posts)1. K&R !!!!!!!!!!!!!!!!!!! n/t
BadGimp
(4,015 posts)2. This stuff is MAD Scarry!
Celerity
(43,398 posts)3. Hackers use fake BSI emails to deliver Sodinokibi ransomware
Sodinokibi ransomware devs started a new malspam campaign: phishing emails sent in the name of national German cybersecurity agency BSI
https://www.2-spyware.com/hackers-use-fake-bsi-emails-to-deliver-sodinokibi-ransomware
A dangerous file-locking and ransom-demanding computer virus named Sodinokibi ransomware[1] has been lately spotted in the wild. Its grand entry was enormous, and it is believed to be the second major malware family of the notorious hacking group behind the already-retired GandCrab.[2]
Although Sodinokibi ransomware has already been actively distributed via exploits and software vulnerabilities, hackers have found ways to push the malware through email spam messages in the name of the national cybersecurity body BSI.
BSI-issued warning[3] claims that sender address of the phishing email is meldung@bsi-bund.org, and warns users about a completely fake data breach. To avoid being a victim of Sodinokibi ransomware developers, users should pay close attention to the Sender address (the original is bsi.bunde.de, not bsi-bund.org), and never open the attachments or click on links inside.
The malicious payload comes inside a ZIP file attachment
Getting a phishing message from threat actors is something that anyone can experience: all it takes is a data breach that leaked personal information previously. The harvested emails are then sold on the underground hacking forums. Thus, anyone can become a target. Those unlucky ones who receive the fake email will see the following bogus message (the note has been translated to English, but its original version is written in the German language):
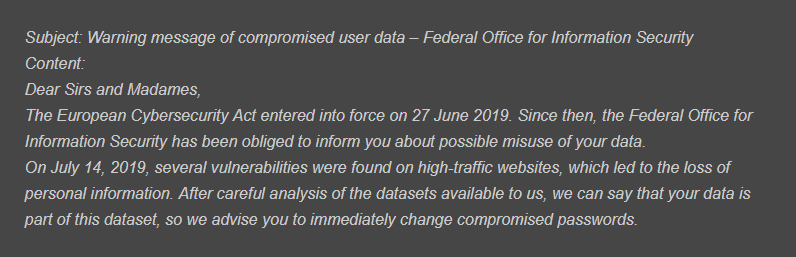
snip
https://www.2-spyware.com/hackers-use-fake-bsi-emails-to-deliver-sodinokibi-ransomware
A dangerous file-locking and ransom-demanding computer virus named Sodinokibi ransomware[1] has been lately spotted in the wild. Its grand entry was enormous, and it is believed to be the second major malware family of the notorious hacking group behind the already-retired GandCrab.[2]
Although Sodinokibi ransomware has already been actively distributed via exploits and software vulnerabilities, hackers have found ways to push the malware through email spam messages in the name of the national cybersecurity body BSI.
BSI-issued warning[3] claims that sender address of the phishing email is meldung@bsi-bund.org, and warns users about a completely fake data breach. To avoid being a victim of Sodinokibi ransomware developers, users should pay close attention to the Sender address (the original is bsi.bunde.de, not bsi-bund.org), and never open the attachments or click on links inside.
The malicious payload comes inside a ZIP file attachment
Getting a phishing message from threat actors is something that anyone can experience: all it takes is a data breach that leaked personal information previously. The harvested emails are then sold on the underground hacking forums. Thus, anyone can become a target. Those unlucky ones who receive the fake email will see the following bogus message (the note has been translated to English, but its original version is written in the German language):

snip