General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsIran Has Been Targeting VPN Servers to Plant Backdoors -- The Larger Context of Our Election Problem
I post this for information purposes, and to show the background problem for broader areas of our nation; that our election vulnerabilities exist among a broader context of others. If any DU'er can shed more light on any terms used in the second diagram, the new learnings would be appreciated.
Cyberwar has always been out there, but this report shows how big it now is from just one state.
What I'm wondering is
-- who sets up all the equipment and hacker expertise in Iran, and
-- who ultimately benefits.
They could just as likely as not be the same people or states.
https://it.slashdot.org/story/20/02/17/0023254/iran-has-been-targeting-vpn-servers-to-plant-backdoors?utm_source=feedburnerFaceBook&utm_medium=feed&utm_campaign=Feed%3A+Slashdot%2Fslashdot+%28Slashdot%29&utm_content=FaceBook&fbclid=IwAR2LSM0pQ_3fc0VxpbjlU2MONY4Ps7Tz7t1ZAYoGpl0EUN4GCtGDX1OUj-o
In some instances, ClearSky says it observed Iranian groups exploiting VPN flaws within hours after the bugs have been publicly disclosed...
According to the ClearSky report, the purpose of these attacks is to breach enterprise networks, move laterally throughout their internal systems, and plant backdoors to exploit at a later date.
https://www.clearskysec.com/fox-kitten/
"Fox Kitten – Widespread Iranian Espionage-Offensive Campaign"
Posted on February 16, 2020 by ClearSky Research Team
During the last quarter of 2019, ClearSky research team has uncovered a widespread Iranian offensive campaign which we call “Fox Kitten Campaign”; this campaign is being conducted in the last three years ...the attackers succeeded in gaining access and persistent foothold in the networks of numerous companies and organizations from the IT, Telecommunication, Oil and Gas, Aviation, Government, and Security sectors around the world.
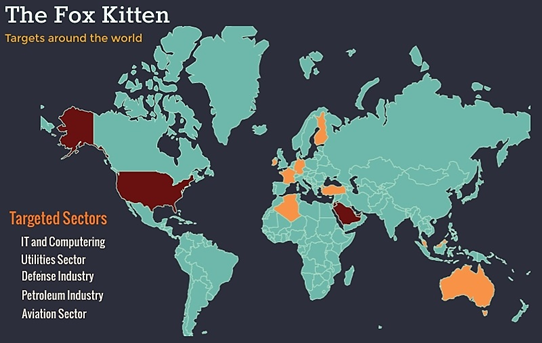
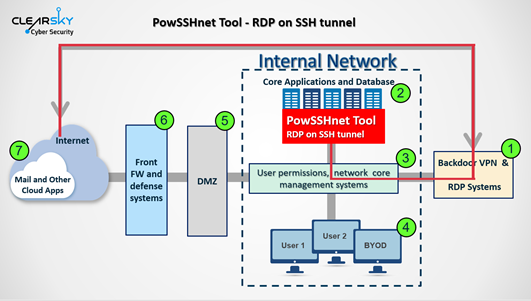
-- The Iranian APT groups have succeeded to penetrate and steal information from dozens of companies around the world in the past three years.
-- The most successful and significant attack vector used by the Iranian APT groups in the last three years has been the exploitation of known vulnerabilities in systems with unpatched VPN and RDP services, in order to infiltrate and take control over critical corporate information storages.
-- This attack vector is not used exclusively by the Iranian APT groups; it became the main attack vector for cybercrime groups, ransomware attacks, and other state-sponsored offensive groups.
...
-- Since 2017, we identify Iranian APT groups focusing on IT companies that provide a wide range of services to thousands of companies. Breaching those IT companies is especially valuable because through them one can reach the networks of additional companies.
-- After breaching the organizations, the attackers usually maintain a foothold and operational redundancy by installing and creating several more access points to the core corporate network. As a result, identifying and closing one access point does not necessarily deny the capability to carry on operations inside the network.
-- We assess with a medium-high probability that Iranian APT groups (APT34 and APT33) share attack infrastructures. Furthermore, it can be one group that was artificially marked in recent years as two or three separate APT groups.
-- The time needed to identify an attacker on a compromised network is long and varies between months to not at all. The existing monitoring capability for organizations to identify and block an attacker that entered through remote communication tools is difficult to impossible.
AnnieBW
(10,426 posts)While not as sophisticated as Russian or Chinese, are still pretty good. One group pulled off the HBO attack a few years ago. They also do a lot with ransomware, especially because they're branching out into stealing Bitcoin wallets. They tend to go after targets in the Middle East, but they do target the U.S.
Stinky The Clown
(67,798 posts)radius777
(3,635 posts)for every candidate, as it is an existential issue, as everything now runs on tech in some form or fashion.
The problem is that the internet/email/etc is fundamentally insecure and was never designed with security in mind.